The Downadup worm—also called Conficker—has now infected an estimated 10 million PCs worldwide, and security experts say they expect to see a dangerous second-stage payload dropped soon.
"It has the potential to infect about 30% of Windows systems online, a potential 300 to 350 million PCs," says Don Jackson, director of threat intelligence in the counter threat unit at SecureWorks. The worm, first identified in November and suspected to have originated in the Ukraine, is quickly ramping up, and while Downadup today is not malicious in the sense of destroying files — its main trick is to block users from accessing antivirus sites to obtain updates to protect against it — the worm is capable of downloading second-stage code for darker purposes. Many experts anticipate that could occur soon.
What that darker purpose might be is a source of speculation, but Jackson theorizes that it will may well end up being "rogue antivirus malware" that demands the user buy it to eliminate the worm. "It's basically extortion," he says.
Like SecureWorks, IBM notes that it's the second stage payload of the Downadup worm that is a source of concern. "Right now it's not destroying or stealing,--it's just hanging out," comments Tom Cross, X-Force researcher in the IBM ISS division. "It's building its network of hosts."
While no one knows exactly what stage two payload will bring, one reason for the worm's somewhat slow but steady progress is its use of Windows "AutoRun" to copy itself through Windows file-sharing and USB tokens, Cross says.
"If it copies itself to a file share, and if the user clicks on a file, the user's computer will get infected," Cross says. "Even if the computer is patched, you can still get infected if you access one of the infected USB drives or file shares." Cross advises that AutoRun be disabled.
This is an additional means of the worm spreading beyond exploiting the Windows RPC flaw identified last October, for which a patch is available. The worm also has a password-cracker that is adept at cracking administrative accounts or other computers, though very strong passwords should make that much harder, Cross says.
Taken From NETWORK WORLD
Computer Virus Malware
The term Malware is used to describe any program that is designed to do harm, although there are different schools of thought as to what is actually harmful.
Adware, Spyware, Viruses, Trojans, Pop-Ups, and even spam have all qualified as computer virus malware.
There are two distinct flavours of Adware. Software supported with advertising is one form or the other more malicious sort. The latter is often termed an Adware Virus whereas the first is just called Adware.
The first could be a useful utility released free of charge but using advertising to generate revenue to support development - similar to TV advertisments. You do not have to watch but if you do you get commercials along with content. Often this type of software is also available in an advertisment free version for a modest price.
The more malicious flavour of Adware virus monitors your browsing and then delivers so called targeted advertisements. This category of software may be considered a type of spyware, especially if it's installed without your knowing and agreement.
When does adware become spyware - well that a somewhat gray area. A number of software vendors claim that disclosing the inclusion of this type of software in the user agreement grants legal consent for its installation. Having said that, how many of us actually read the small print before installing software!
A Spyware virus on the other hand, can have a more insidious meaning. The term Spyware, can refer to software which does much more than simply monitor a user's browsing habits. It can often redirect your browser to completely different sites the majority of which are advertising sites.
This form of Spyware virus is nearly always installed without the user's knowledge and hidden within another program. It can also arrive as the payload of a worm or virus. It's also illegal in many countries. In the U.S. the Federal Trade Commission or FTC has indicted, and in some cases convicted, several purveyors.
Some software suppliers will require that the user install spyware as part of a package. Its inclusion is declared in the user agreement but users do not have the option of not installing it. If the user wants the main program they have to install the spyware as well. File sharing utilities like Kazaa or BearShare are notorious for this practice.
The spyware installed with these, and many other, programs collect information in respect of web browsing habits and then deliver targeted advertising to the user. Targeted advertising is designed to be presented to specific groups, selected by analyzing their buying or browsing habits. Selections are made by discovering gender, age or frequently visited sites or by various other undisclosed criteria.
Spyware vendors argue that it does not collect specific personal information and there is an active debate as to whether it constitutes legitimate market analysis or a violation of personal privacy..
The majority of users find it annoying and intrusive. However, advertisers claim it to be the best way to deliver products and services to potential new customers who may actually end up buying what is offered. Legally, they assert, it is just another form of free speech. Users on the other hand respond that the advertisers free speech does not reach to their browser or email Inbox.
Adware, Spyware, Viruses, Trojans, Pop-Ups, and even spam have all qualified as computer virus malware.
There are two distinct flavours of Adware. Software supported with advertising is one form or the other more malicious sort. The latter is often termed an Adware Virus whereas the first is just called Adware.
The first could be a useful utility released free of charge but using advertising to generate revenue to support development - similar to TV advertisments. You do not have to watch but if you do you get commercials along with content. Often this type of software is also available in an advertisment free version for a modest price.
The more malicious flavour of Adware virus monitors your browsing and then delivers so called targeted advertisements. This category of software may be considered a type of spyware, especially if it's installed without your knowing and agreement.
When does adware become spyware - well that a somewhat gray area. A number of software vendors claim that disclosing the inclusion of this type of software in the user agreement grants legal consent for its installation. Having said that, how many of us actually read the small print before installing software!
A Spyware virus on the other hand, can have a more insidious meaning. The term Spyware, can refer to software which does much more than simply monitor a user's browsing habits. It can often redirect your browser to completely different sites the majority of which are advertising sites.
This form of Spyware virus is nearly always installed without the user's knowledge and hidden within another program. It can also arrive as the payload of a worm or virus. It's also illegal in many countries. In the U.S. the Federal Trade Commission or FTC has indicted, and in some cases convicted, several purveyors.
Some software suppliers will require that the user install spyware as part of a package. Its inclusion is declared in the user agreement but users do not have the option of not installing it. If the user wants the main program they have to install the spyware as well. File sharing utilities like Kazaa or BearShare are notorious for this practice.
The spyware installed with these, and many other, programs collect information in respect of web browsing habits and then deliver targeted advertising to the user. Targeted advertising is designed to be presented to specific groups, selected by analyzing their buying or browsing habits. Selections are made by discovering gender, age or frequently visited sites or by various other undisclosed criteria.
Spyware vendors argue that it does not collect specific personal information and there is an active debate as to whether it constitutes legitimate market analysis or a violation of personal privacy..
The majority of users find it annoying and intrusive. However, advertisers claim it to be the best way to deliver products and services to potential new customers who may actually end up buying what is offered. Legally, they assert, it is just another form of free speech. Users on the other hand respond that the advertisers free speech does not reach to their browser or email Inbox.
Spyware and Adware
As well as being an annoyance, badly programmed adware and spyware can interfere with other programs and can even cause your computer system to become unstable. Issues of Privacy also come into play as well.
This type of software is usually installed without a user's consent and many times cannot be uninstalled without special tools. When distributors use tricks and deceit to install uninvited software, trust is destroyed.
Instead of having to use a Spyware Remover or Remove Adware as a last resort, you can and should take steps to protect yourself from the threat.
The first line of defense against adware and spyware is to be cautious when installing software. Understand what is being downloaded and also where you are downloading from. A lot of so called freeware and shareware programs have spyware embedded in them, which is not always disclosed.
Before downloading any new software, look for guarantees that it is adware and spyware free. Even so, be on your guard. For instance, the file sharing program Kazaa has been claiming to be spyware free for years but anyone who installs this software soon has an chance to test this claim.
How can you tell if you have adware or spyware on your system? You may see pop up advertisements even when you are not browsing the web. Your browser home page may have been changed without your knowledge. New toolbars may appear on your browser which you did not install. Your computer may be very slow or unexplainably reboot on its own. although, the last effect is most often a virus.
If you find that your computer system bogged down with adware or spyware, don't give up hope. There are some spyware remover utilities specifically designed to remove adware and from your computer. They rely on regularly updated databases which hold signature files of all known adware and spyware. The program will scan all of the files on your hard drive and alert you if anything untoward is discovered.
Many of these spyware remover utilities are free, although sometimes the paid versions have more automation features such as remove adware on receipt rather than requiring a manual scan. None will find every piece of spyware on your computer system, since they rely on a database which has to be populated according to someone's judgment. And, one man's spyware is sometimes another's welcomed advertiser.
You may find that even with a spyware remover utilty, some spyware is next to impossible to remove. Alterations to system settings and the installation of files in different places makes the job of detection and removal very difficult. Sometimes it is only possible to remove this type of spyware manually.
To remove adware from your computer is a skilled job and should only be performed by users who know what they are doing as the deletion of the wrong files can potentially damage your programs and even your operating system.
One spyware remover utility that can be of big assistance in your quest to remove difficult spyware is called 'HijackThis'. This utility creates a list of files which may have been altered by spyware. The list is very comprehensive and also includes system files and files installed by legitimate software, so be very careful when using it.
Although HijackThis was not initially designed to be a spyware remover tool, it can be used to great effect in locating persistent and hard to remove spyware. It requires a good knowledge of various system settings and you must be extra careful when changing them. Making the wrong setting can quite easily disable your computer system. However, there is a community of HijackThis experts on the Internet that are more than willing to give free advice about suspicious entries.
Once your system is spyware free help keep it that way. Some spyware remover software used to remove adware also includes additional utilities that will protect your computer in real time. Similar to virus scanners, they monitor for any changes to your system files and alert you of any suspicious activity that is detected.
This type of software is usually installed without a user's consent and many times cannot be uninstalled without special tools. When distributors use tricks and deceit to install uninvited software, trust is destroyed.
Instead of having to use a Spyware Remover or Remove Adware as a last resort, you can and should take steps to protect yourself from the threat.
The first line of defense against adware and spyware is to be cautious when installing software. Understand what is being downloaded and also where you are downloading from. A lot of so called freeware and shareware programs have spyware embedded in them, which is not always disclosed.
Before downloading any new software, look for guarantees that it is adware and spyware free. Even so, be on your guard. For instance, the file sharing program Kazaa has been claiming to be spyware free for years but anyone who installs this software soon has an chance to test this claim.
How can you tell if you have adware or spyware on your system? You may see pop up advertisements even when you are not browsing the web. Your browser home page may have been changed without your knowledge. New toolbars may appear on your browser which you did not install. Your computer may be very slow or unexplainably reboot on its own. although, the last effect is most often a virus.
If you find that your computer system bogged down with adware or spyware, don't give up hope. There are some spyware remover utilities specifically designed to remove adware and from your computer. They rely on regularly updated databases which hold signature files of all known adware and spyware. The program will scan all of the files on your hard drive and alert you if anything untoward is discovered.
Many of these spyware remover utilities are free, although sometimes the paid versions have more automation features such as remove adware on receipt rather than requiring a manual scan. None will find every piece of spyware on your computer system, since they rely on a database which has to be populated according to someone's judgment. And, one man's spyware is sometimes another's welcomed advertiser.
You may find that even with a spyware remover utilty, some spyware is next to impossible to remove. Alterations to system settings and the installation of files in different places makes the job of detection and removal very difficult. Sometimes it is only possible to remove this type of spyware manually.
To remove adware from your computer is a skilled job and should only be performed by users who know what they are doing as the deletion of the wrong files can potentially damage your programs and even your operating system.
One spyware remover utility that can be of big assistance in your quest to remove difficult spyware is called 'HijackThis'. This utility creates a list of files which may have been altered by spyware. The list is very comprehensive and also includes system files and files installed by legitimate software, so be very careful when using it.
Although HijackThis was not initially designed to be a spyware remover tool, it can be used to great effect in locating persistent and hard to remove spyware. It requires a good knowledge of various system settings and you must be extra careful when changing them. Making the wrong setting can quite easily disable your computer system. However, there is a community of HijackThis experts on the Internet that are more than willing to give free advice about suspicious entries.
Once your system is spyware free help keep it that way. Some spyware remover software used to remove adware also includes additional utilities that will protect your computer in real time. Similar to virus scanners, they monitor for any changes to your system files and alert you of any suspicious activity that is detected.
Kaspersky Two Top Twenties Virus
Pingin tahu urutan Virus/Worm di dunia?
Berikut ini saya kutip dari www.kaspersky.com
======== Kaspersky Two Top Twenties Virus ==========
Two Top Twenties Virus have been compiled from data generated by the Kaspersky Security Network (KSN) throughout January 2009.
The first Top Twenty is based on data collected by Kaspersky Lab’s 2009 antivirus product and gives details of malicious, advertising, and potentially unwanted programs detected on users’ computers.
1. Virus.Win32.Sality.aa
2. Packed.Win32.Krap.b
3. Worm.Win32.AutoRun.dui
4. Trojan-Downloader.Win32.VB.eql
5. Trojan.Win32.Autoit.ci
6. Trojan-Downloader.WMA.GetCodec.c
7. Packed.Win32.Black.a
8. Virus.Win32.Alman.b
9. Trojan.Win32.Obfuscated.gen
10. Trojan-Downloader.WMA.GetCodec.r
11. Exploit.JS.Agent.aak
12. Worm.Win32.Mabezat.b
13. Worm.Win32.AutoIt.ar
14. Email-Worm.Win32.Brontok.q
15. Virus.Win32.Sality.z
16. Net-Worm.Win32.Kido.ih
17. Trojan-Downloader.WMA.Wimad.n
18. Virus.Win32.VB.bu
19. Trojan.Win32.Agent.abt
20. Worm.Win32.AutoRun.vnq
There were no major changes to the composition of the first Top Twenty during the first month of 2009. Exploit.JS.Agent.aak took the place of Trojan.HTML.Agent.ai and Trojan-Downloader.JS.Agent.czm which appeared in the December ratings. The AutoRun.eee worm, which has vanished from this month’s Top Twenty, has now been replaced by Worm.Win32.AutoRun.vnq. This is not surprising, as frequent new modifications are characteristic of these types of malicious program.
Trojan-Downloader.WMA.Wimad.n, which dropped out of the ratings in November, has also returned to the game. The result of this activity is a Top Twenty Virus with three non-standard downloader programs; evidence of the mass spread of this type of Trojan program, and the trusting attitude users have towards multi-media files. The sharp rise of Trojan-Downloader.WMA.GetCodec.r by ten places confirms that the propagation method described in last month’s Top Twenty, whereby malicious programs use peer-to-peer networks and multimedia downloaders to spread has been very effective.
While Sality.aa still retains its leading position, it has been joined by Sality.z, making Sality one of the most widespread and dangerous families of the recent past.
The notorious Kido family, network worms which use a critical vulnerability in Microsoft Windows to spread, is also present. The current epidemic, the propagation method used, and the number of potentially vulnerable computers mean the appearance of Kido variants in this month’s Top Twenty are no surprise.
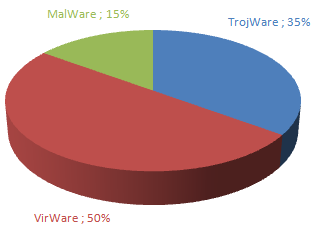
All malicious, advertising and potentially unwanted programs in the first Top Twenty can be grouped according to the main classes of threats which we detect. Self-replicating programs again prevail over Trojan programs.
In total, 46014 unique malicious, advertising, and potentially unwanted programs were detected on users’ computers in January. It should be noted that the holiday period did not result in a drop in threats found “in-the-wild”; on the contrary, there were 7800 more “in-the-wild” samples detected than in December (38190).
The second Top Twenty Virus presents data on which malicious programs most commonly infected objects detected on users’ computers. Malicious programs capable of infecting files make up the majority of this ranking.
1. Virus.Win32.Sality.aa
2. Worm.Win32.Mabezat.b
3. Net-Worm.Win32.Nimda
4. Virus.Win32.Xorer.du
5. Virus.Win32.Alman.b
6. Virus.Win32.Sality.z
7. Virus.Win32.Parite.b
8. Virus.Win32.Virut.q
9. Trojan-Downloader.HTML.Agent.ml
10. Virus.Win32.Virut.n
11. Email-Worm.Win32.Runouce.b
12. Worm.Win32.Otwycal.g
13. P2P-Worm.Win32.Bacteraloh.h
14. Virus.Win32.Hidrag.a
15. Virus.Win32.Small.l
16. Virus.Win32.Parite.a
17. Worm.Win32.Fujack.bd
18. P2P-Worm.Win32.Deecee.a
19. Trojan.Win32.Obfuscated.gen
20. Virus.Win32.Sality.y
Sality.z was the latest representative of Virus.Win32.Sality to make it into the first Top Twenty. Sality.y has appeared in the second Top Twenty, confirming again the high activity of this family of self-replicating programs.
An interesting newcomer to the second rating is P2P-Worm.Win32.Deecee.a. This worm spreads via the DC++ peer-to-peer network, and is capable of downloading other malicious files. It has gained a place in the second Top Twenty Virus not so much because of the number of machines it has infected, but because of the number of copies of itself on every infected computer - it copies itself multiple times when installing. Once installed, this worm makes the copies of itself publicly accessible. The executable files which spread in this way have names which follow a set pattern: a prefix such as “(CRACK)”, “(PATCH)”, then the name of a popular application: “ADOBE ILLUSTRATOR (All Versions)”, “GTA SAN ANDREAS ACTION 1 DVD”, etc.
Worm.VBS.Headtail.a, which returned to the rankings in November, has disappeared again, continuing to exhibit the unstable behaviour which we noted towards the end of 2008.
=================== End =================
Semoga Bermanfaat.
Berikut ini saya kutip dari www.kaspersky.com
======== Kaspersky Two Top Twenties Virus ==========
Two Top Twenties Virus have been compiled from data generated by the Kaspersky Security Network (KSN) throughout January 2009.
The first Top Twenty is based on data collected by Kaspersky Lab’s 2009 antivirus product and gives details of malicious, advertising, and potentially unwanted programs detected on users’ computers.
1. Virus.Win32.Sality.aa
2. Packed.Win32.Krap.b
3. Worm.Win32.AutoRun.dui
4. Trojan-Downloader.Win32.VB.eql
5. Trojan.Win32.Autoit.ci
6. Trojan-Downloader.WMA.GetCodec.c
7. Packed.Win32.Black.a
8. Virus.Win32.Alman.b
9. Trojan.Win32.Obfuscated.gen
10. Trojan-Downloader.WMA.GetCodec.r
11. Exploit.JS.Agent.aak
12. Worm.Win32.Mabezat.b
13. Worm.Win32.AutoIt.ar
14. Email-Worm.Win32.Brontok.q
15. Virus.Win32.Sality.z
16. Net-Worm.Win32.Kido.ih
17. Trojan-Downloader.WMA.Wimad.n
18. Virus.Win32.VB.bu
19. Trojan.Win32.Agent.abt
20. Worm.Win32.AutoRun.vnq
There were no major changes to the composition of the first Top Twenty during the first month of 2009. Exploit.JS.Agent.aak took the place of Trojan.HTML.Agent.ai and Trojan-Downloader.JS.Agent.czm which appeared in the December ratings. The AutoRun.eee worm, which has vanished from this month’s Top Twenty, has now been replaced by Worm.Win32.AutoRun.vnq. This is not surprising, as frequent new modifications are characteristic of these types of malicious program.
Trojan-Downloader.WMA.Wimad.n, which dropped out of the ratings in November, has also returned to the game. The result of this activity is a Top Twenty Virus with three non-standard downloader programs; evidence of the mass spread of this type of Trojan program, and the trusting attitude users have towards multi-media files. The sharp rise of Trojan-Downloader.WMA.GetCodec.r by ten places confirms that the propagation method described in last month’s Top Twenty, whereby malicious programs use peer-to-peer networks and multimedia downloaders to spread has been very effective.
While Sality.aa still retains its leading position, it has been joined by Sality.z, making Sality one of the most widespread and dangerous families of the recent past.
The notorious Kido family, network worms which use a critical vulnerability in Microsoft Windows to spread, is also present. The current epidemic, the propagation method used, and the number of potentially vulnerable computers mean the appearance of Kido variants in this month’s Top Twenty are no surprise.

All malicious, advertising and potentially unwanted programs in the first Top Twenty can be grouped according to the main classes of threats which we detect. Self-replicating programs again prevail over Trojan programs.
In total, 46014 unique malicious, advertising, and potentially unwanted programs were detected on users’ computers in January. It should be noted that the holiday period did not result in a drop in threats found “in-the-wild”; on the contrary, there were 7800 more “in-the-wild” samples detected than in December (38190).
The second Top Twenty Virus presents data on which malicious programs most commonly infected objects detected on users’ computers. Malicious programs capable of infecting files make up the majority of this ranking.
1. Virus.Win32.Sality.aa
2. Worm.Win32.Mabezat.b
3. Net-Worm.Win32.Nimda
4. Virus.Win32.Xorer.du
5. Virus.Win32.Alman.b
6. Virus.Win32.Sality.z
7. Virus.Win32.Parite.b
8. Virus.Win32.Virut.q
9. Trojan-Downloader.HTML.Agent.ml
10. Virus.Win32.Virut.n
11. Email-Worm.Win32.Runouce.b
12. Worm.Win32.Otwycal.g
13. P2P-Worm.Win32.Bacteraloh.h
14. Virus.Win32.Hidrag.a
15. Virus.Win32.Small.l
16. Virus.Win32.Parite.a
17. Worm.Win32.Fujack.bd
18. P2P-Worm.Win32.Deecee.a
19. Trojan.Win32.Obfuscated.gen
20. Virus.Win32.Sality.y
Sality.z was the latest representative of Virus.Win32.Sality to make it into the first Top Twenty. Sality.y has appeared in the second Top Twenty, confirming again the high activity of this family of self-replicating programs.
An interesting newcomer to the second rating is P2P-Worm.Win32.Deecee.a. This worm spreads via the DC++ peer-to-peer network, and is capable of downloading other malicious files. It has gained a place in the second Top Twenty Virus not so much because of the number of machines it has infected, but because of the number of copies of itself on every infected computer - it copies itself multiple times when installing. Once installed, this worm makes the copies of itself publicly accessible. The executable files which spread in this way have names which follow a set pattern: a prefix such as “(CRACK)”, “(PATCH)”, then the name of a popular application: “ADOBE ILLUSTRATOR (All Versions)”, “GTA SAN ANDREAS ACTION 1 DVD”, etc.
Worm.VBS.Headtail.a, which returned to the rankings in November, has disappeared again, continuing to exhibit the unstable behaviour which we noted towards the end of 2008.
=================== End =================
Semoga Bermanfaat.
Suara Hati Seorang Pemuda Kecil Indonesia
Suara Hati Seorang Pemuda Kecil Indonesia
Sedikit mengeluarkan isi hati melihat keangkuhan
yang selalu dibanggakan,saya hanya seorang pemuda
kecil yang berangan-angan mempunyai tempat layak nya
istana khayangan yang indah akan perdamaian tanpa
saling caci-maki. Saling merendahkan, menjatuhkan,
membuat kontrofersi, menganggap paling bersih tanpa
pernah tersentuh sebuah skandal.. BULLLLSSSHIIIITTT
Hidup diantara perbedaan yang tanpa pernah disatukan
seakan tebelenggu dalam sebuah bejana racun nomor satu,
hampa hidup perlahan seakan mati tanpa sebuah perjuangan.
Mereka selalu bernyanyi bak kicau burung gagak yang
angkuh mengepakakan sayap di antara sudut hidupku, saya
No 1, saya terbersih, saya paling pantas anda sanjungkan.
Pahit, muak mendengar perkataan tersebut.
Apakah ada kesadaraan dalam lubuk hati nya?? Pecahan riak
air di setiap pandangan ku melayangkan ku pada angan yang
telah terbang menghilang mejauh dari pandangan. Seorang pemuda
ini hanya bisa meratapi akan gejolak pertarungan para penguasa,
saling tikam-menikam tanpa mengindahkan bahwa kita saudara, satu
tanah air ibu pertiwi indonesia.
Pekat hitam kelam terpampang secara gamblang di hadapan, langkah
terengah seakan harus terhenti pada sebuah realita ketidak benaran.
Ibu, akankah engkau harus terus menangis dalam jalan mu menuju
akhir, dalam setiap detik waktu jantung mu berdetak...
Tiada kuasa pemuda kecil indonesia ini berjuang untuk mu ibu, tangan kekuasaan
merenggut keindahan dari norma kebersamaan, hidupku hanya mampu termenung
di kelilingi ke angkuhan yang berebut untuk kesucian mu ibu.
Wahai ibu pertiwi ku Indonesia terus lah dirimu berjalan walau setapak,
walau pahit getir disekitarmu, walau keangkuhan merajalela, tutup telinga mu ibu
hiraukan saja anjing kecil itu menggonggong mengagungkan kesombongan nya di seluruh
sudut Indonesiaku.
Wahai engkau Bhineka Tunggal Ika ku, terus lah dirimu tegap menghadapi
perdebatan kotor di sekeliling mu, jangan pernah engkau melepaskan gemulai
jemari mu dari pundak ku, jika ku sanggup kan kuhapus setiap titik air mata
dirimu agar kita bersama maju menghilangkan sosok ke angkuhan itu, mempersatukan
perbedaan yang ada, menghilangkan kata-kata manis palsu dari tiap langkah
kita.
Sembah sujud ku pada-MU ya Tuhan ku yang Kuasa, berilah aku arti untuk
menutup ke angkuhan itu, membongkar tabir kebenaran dari tirai kesombongan
yang mengelilingi pandangan indah ku. Semoga hingga akhir nanti kita
masih mampu berjalan bergandengan tangan.
Ini hanya suara hati dari seorang pemuda kecil indonesia.
Mencetak lebih cepat lewat Command Prompt
Mencetak lebih cepat lewat Command Prompt.
Sistem operasi Microsoft Windows 2000 merupakan salah satu sistem operasi yang cukup tangguh untuk urusan jaringan. Karenanya, tak heran jika banyak korporasi yang menggunakan sistem operasi ini pada seluruh komputer yang terkoneksi ke jaringan.
Tak jarang, program-program berbasis DOS masih tetap digunakan walaupun sistem operasi utama Anda adalah Windows 2000. Tindakan Anda tidak salah, karena program-program tersebut tetap dapat bekerja dengan baik dan cepat di atas sistem operasi Windows 2000. Hanya saja, untuk urusan pencetakan Windows 2000 memiliki sedikit masalah dengan program-program berbasis DOS. Respon saat melakukan pencetakan terasa lebih lambat dibandingkan saat mencetak dokumen yang dibuka oleh aplikasi berbasis Windows.
Solusi dari permasalahan diatas dapat Anda lakukan dengan cara:
1. Jalankan Registry Editor dengan mengklik [Start] kemudian ketik regedit.exe.
2. Masuklah ke subkey HKEY_LOCAL_MACHINE-SYSTEM-CurrentControlSet-Control-WOW.
3. Carilah String Value dengan nama LPT_timeout, kemudian klik ganda String Value tersebut.
4. Ubahlah Value Data yang sebelumnya bernailai 15 menjadi 3.
5. Klik [OK] lalu tutup jendela Registry Editor. Sekarang, cobalah untuk mencetak kembali melalui Command Prompt.
Selamat Mencoba.
sumber: PCplus
Sistem operasi Microsoft Windows 2000 merupakan salah satu sistem operasi yang cukup tangguh untuk urusan jaringan. Karenanya, tak heran jika banyak korporasi yang menggunakan sistem operasi ini pada seluruh komputer yang terkoneksi ke jaringan.
Tak jarang, program-program berbasis DOS masih tetap digunakan walaupun sistem operasi utama Anda adalah Windows 2000. Tindakan Anda tidak salah, karena program-program tersebut tetap dapat bekerja dengan baik dan cepat di atas sistem operasi Windows 2000. Hanya saja, untuk urusan pencetakan Windows 2000 memiliki sedikit masalah dengan program-program berbasis DOS. Respon saat melakukan pencetakan terasa lebih lambat dibandingkan saat mencetak dokumen yang dibuka oleh aplikasi berbasis Windows.
Solusi dari permasalahan diatas dapat Anda lakukan dengan cara:
1. Jalankan Registry Editor dengan mengklik [Start] kemudian ketik regedit.exe.
2. Masuklah ke subkey HKEY_LOCAL_MACHINE-SYSTEM-CurrentControlSet-Control-WOW.
3. Carilah String Value dengan nama LPT_timeout, kemudian klik ganda String Value tersebut.
4. Ubahlah Value Data yang sebelumnya bernailai 15 menjadi 3.
5. Klik [OK] lalu tutup jendela Registry Editor. Sekarang, cobalah untuk mencetak kembali melalui Command Prompt.
Selamat Mencoba.
sumber: PCplus
Algoritma Virus
Algoritma Virus?? Waduh, susah neh seperti nya,
ada yang bisa bantu saya? he..he.
Kok Virus pake Algoritma juga ya? Ya harus dong
agar virus yang kita buat benar-benar berjalan
dengan baik pada saat peyerangan dan pertahanan
nya. Langsung saja ya sob meng analisis Algoritma
dari si Virus.
Seperti apa Algoritma Virus itu? seperti ini dalam
uraian singkat saja..
1. Sebuah Virus itu harus mempunyai/membuat file Induk
terlebih dahulu karena itulah inti dari virus tersebut.
2. Si Virus harus mampu meng Infeksi drive lain secara otomatis,
seperti Drive untuk FlashDisk atau mecari file sehat yang akan
di infeksi.
3. Virus harus mampu mematikan beberapa system dari sebuah
Operating System seperti Task Manager, CMD, Folder Option
dll deh, dengan cara masuk melalui "Registry" pada System
Operating tersebut.
4. Virus harus mampu melakukan tipuan mata seperti menyamar
menjadi Icon file bawaan System Operasi tersebut.
5. Virus di usahakan jangan terlalu menampakkan dirinya,
misalkan Pamer dengan berlebihan. Jika berlebihan itu
akan menjadi kelemahan sebuah virus, mudah terdeteksi
keberadaan nya.
Oke, untuk lebih lengkapnya tentang Algoritma Virus silahkan sobat
kunjungi blog saya yang Belajar dan Berbagi.
Thanks..
Di ambil dari http://aalil.blogspot.com/
ada yang bisa bantu saya? he..he.
Kok Virus pake Algoritma juga ya? Ya harus dong
agar virus yang kita buat benar-benar berjalan
dengan baik pada saat peyerangan dan pertahanan
nya. Langsung saja ya sob meng analisis Algoritma
dari si Virus.
Seperti apa Algoritma Virus itu? seperti ini dalam
uraian singkat saja..
1. Sebuah Virus itu harus mempunyai/membuat file Induk
terlebih dahulu karena itulah inti dari virus tersebut.
2. Si Virus harus mampu meng Infeksi drive lain secara otomatis,
seperti Drive untuk FlashDisk atau mecari file sehat yang akan
di infeksi.
3. Virus harus mampu mematikan beberapa system dari sebuah
Operating System seperti Task Manager, CMD, Folder Option
dll deh, dengan cara masuk melalui "Registry" pada System
Operating tersebut.
4. Virus harus mampu melakukan tipuan mata seperti menyamar
menjadi Icon file bawaan System Operasi tersebut.
5. Virus di usahakan jangan terlalu menampakkan dirinya,
misalkan Pamer dengan berlebihan. Jika berlebihan itu
akan menjadi kelemahan sebuah virus, mudah terdeteksi
keberadaan nya.
Oke, untuk lebih lengkapnya tentang Algoritma Virus silahkan sobat
kunjungi blog saya yang Belajar dan Berbagi.
Thanks..
Di ambil dari http://aalil.blogspot.com/
Langganan:
Postingan (Atom)

